Mark Read, head of data breach solutions for TransUnion in the UK, shares insights on the current data breach landscape, including how businesses should respond to a data breach to reduce impact. Watch the video blog to gain insight into the data breach landscape.
Cyber Risk Audit
Threats from cyberattacks are significant and constantly changing. Performing periodic, internal audits of your risk profile and cybersecurity is critical to managing the never-ending battle against cyber threats. At ONIT Technology Solutions, we offer an independent assessment of your cyber risks and existing and required controls. Receive a complimentary cyber risk audit when you schedule direct.
Cybersecurity Agencies Release Guidance for PowerShell Security
PowerShell is a common program hackers use in “living off the land” attacks, a strategy deployed by malicious actors to use an organization’s tools against itself. PowerShell is also a Microsoft command line tool for patching systems and executing scripts. How can you use PowerShell safely? Read this blog summarizing recommendations from the U.S. Cybersecurity and Infrastructure Security Agency and counterparts in the UK and New Zealand.
Allied Cybersecurity Agencies Advise Against Disabling Popular Tool for Cyberattackers
The Microsoft program, PowerShell, has granted malicious actors remote command and control of victims in hacking schemes. But it can also improve cybersecurity management. This blog discusses how the threat can be mitigated by proper configuration. Read the blog before removing it recommends a joint advisory from the Cybersecurity and Infrastructure Security Agency, National Security Agency and allied counterparts.
Cybersecurity team assessment
Cybersecurity is a high-demand, high-profile profession with acute staffing shortages. Facing a fierce recruiting environment, smart organizations are learning to be more creative and flexible as they strive to build resilient, sustainable cybersecurity teams. Let the experts at ONIT Technology Solutions help you improve your cybersecurity team and close the skills gap at your organization.
Not Enough Entry-Level Cyber Pros?
Despite the fact the cybersecurity skills gap continues to widen, many organizations still believe they can find cybersecurity veterans to fill out their security team rosters. Read the blog to gain insight on why filling entry-level roles has become a major problem.
Microsoft Surface Laptop 3
This video presents the unique features of the Microsoft Surface Laptop 3 in connected work environments and everyday entertainment. The clip highlights several robust capabilities, such as instant-on and fast charging, which cater to always-connected lifestyles. A wide precision trackpad (20% larger than previous models) ensures quick access to applications. For more information about the Microsoft Surface Laptop 3, contact us today.
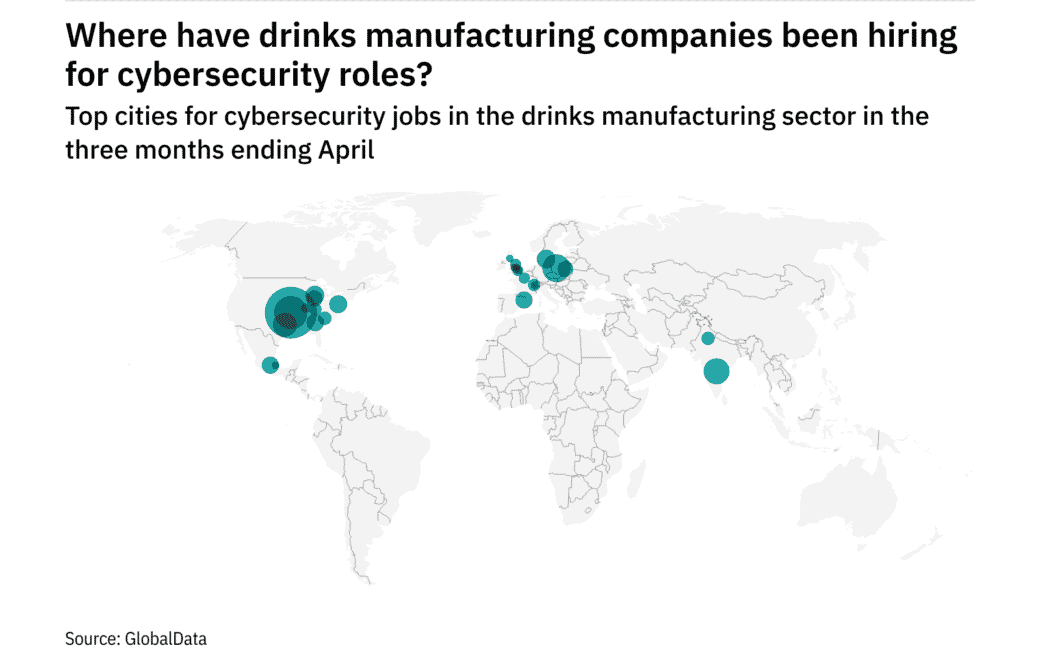
North America Sees Hiring Boom in Drinks Industry Cybersecurity Roles
The drinks industry is leading the charges when it comes to cybersecurity hiring in North America. Read the article to gain insight on how the hirings in this sector in the U.S. are growing fast.
Keys to Designing your Modern Workplace
This eBook provides insights on factors that contribute to functional, modern workplaces. With 41% of employees spending more time away from their desks than they did 2 years ago, changes to the way offices are designed and electronics are accessed should be made to support creativity. The right set of technology, such as audio conferencing, open guest Wi-Fi, and wireless projectors, could help tech-savvy workers become more productive and boost overall morale. Contact us today for more information about Microsoft products for modern workplaces.